In today’s hyperconnected world, cyberattacks have become more frequent, more sophisticated, and more damaging. Whether you’re an individual, a small business owner, or part of a large corporation, understanding how attackers operate is the first step toward protecting your digital life.
In this article, we’ll break down seven common types of cyberattacks you may face today, along with practical ways to prevent them.
1. Phishing
What it is: A technique where attackers impersonate legitimate entities—usually via email—to trick you into revealing personal data like login credentials, credit card numbers, or other sensitive information.
How to avoid it:
-
Never click on suspicious links or download unknown attachments.
-
Always verify the sender’s identity.
-
Use email filtering and security awareness training.

2. Ransomware
What it is: Malicious software that encrypts your files and demands payment (usually in cryptocurrency) to restore access.
How to avoid it:
-
Keep all software and operating systems up to date.
-
Regularly back up your data on offline or secure cloud systems.
-
Avoid downloading files from untrusted sources.

3. DDoS Attacks (Distributed Denial of Service)
What it is: An overload of traffic sent to a network or server to make it unavailable to users. These attacks are often used to take down websites or disrupt services.
How to avoid it:
-
Use a reliable Content Delivery Network (CDN) with DDoS protection.
-
Set up firewall rules and traffic monitoring systems.
-
Work with your hosting provider for mitigation strategies.
4. Brute Force Attacks
What it is: An attack where hackers systematically try every possible password combination until they gain access.
How to avoid it:
-
Use strong, complex passwords and change them regularly.
-
Enable Multi-Factor Authentication (MFA).
-
Limit login attempts and monitor access logs.

5. Malware and Spyware
What it is: Malicious software that installs itself on your device to steal information, track your activity, or damage files.
How to avoid it:
-
Install and update antivirus/antimalware software.
-
Don’t download software or open attachments from unknown sources.
-
Keep your browser and plugins up to date.

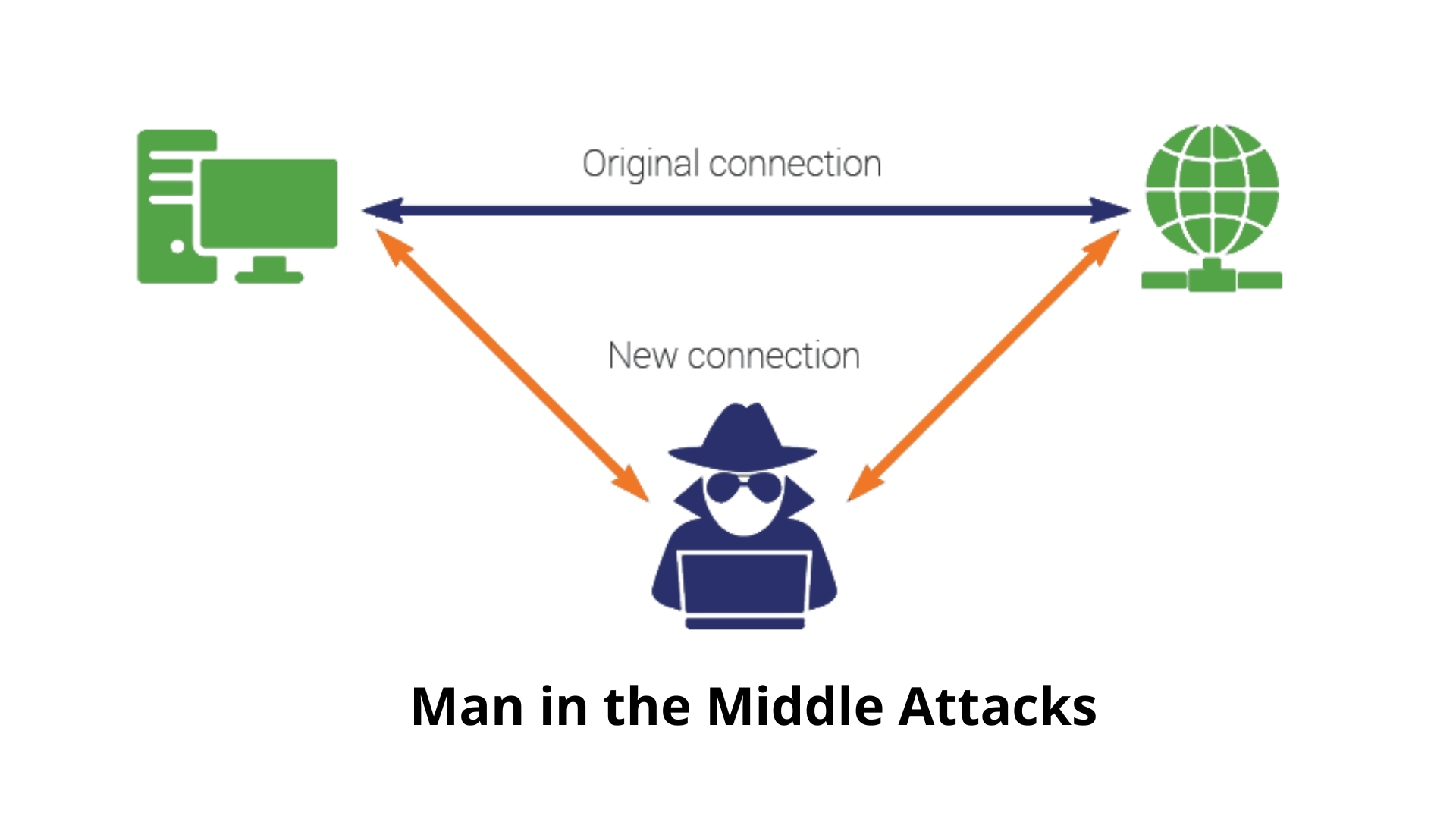
6. Man in the Middle Attacks (MitM)
What it is: When a hacker secretly intercepts and possibly alters the communication between two parties without their knowledge.
How to avoid it:
-
Avoid using public Wi-Fi for sensitive transactions.
-
Use VPNs and encrypted communication protocols (HTTPS, SSL/TLS).
-
Keep your devices updated with the latest security patches.
7. Exploiting Software Vulnerabilities
What it is: Hackers take advantage of unpatched software vulnerabilities to gain control or access systems.
How to avoid it:
-
Regularly update all applications and systems.
-
Use vulnerability scanning tools.
-
Employ patch management strategies.

Cyberattacks are not just a concern for big corporations—anyone can be a target. The key to protection is awareness, prevention, and constant vigilance. By understanding the types of attacks and how to defend against them, you reduce the risk of falling victim and help create a safer digital environment for all.


