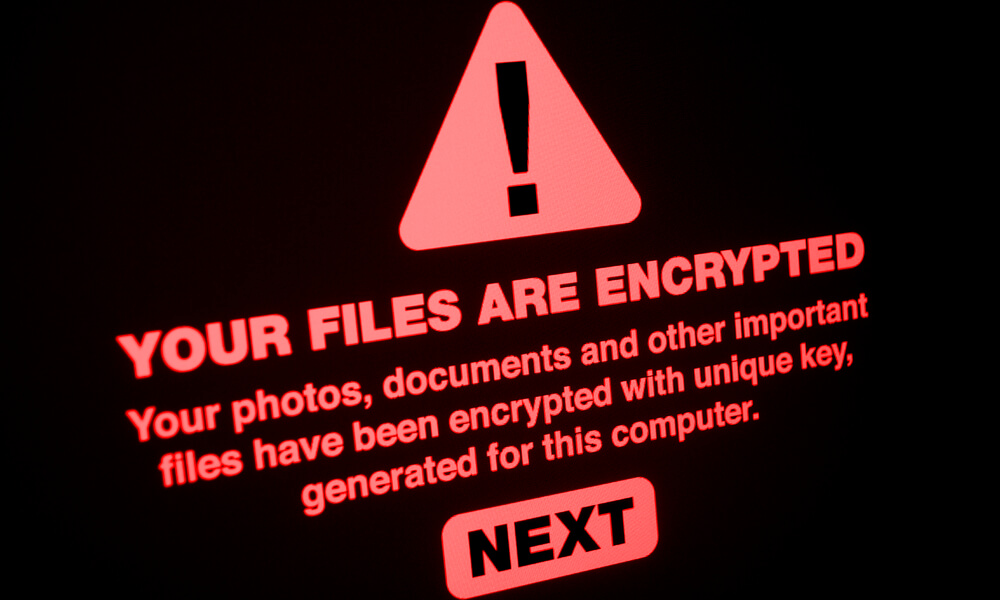
Pysa is just one of many ransomware programs out there. These are generally designed to prevent victims from accessing their data by encrypting them with a strong cryptographic algorithm and creating or displaying a ransom message which asks for a sum of money to be able to recover this data.
Generally, only cyber criminals have tools that can decrypt files encrypted by their ransomware. Therefore, it is impossible to decrypt files, unless the ransomware is incomplete and contains flaws or vulnerabilities that we can take advantage of this.
What happend if you get infected with the Pysa ransomware
The infection procedure for this ransomware downloads and executes a PowerShell script that ends various system processes and keeps the RDP protocol running to exfiltrate the collected information to a C2 command and control server. The ransomware in charge is then executed to encrypt the files of the compromised computers by adding the extension .pysa.
Getting infected with this threat allows:
▸Scheduled persistence of tasks to execute malicious file
▸Credential dump through task manager
▸Access to shadow copy ntds.dit, which stores information on objects (users, computers, etc.) of the domain within the active directory
▸Running miscellaneous malware on the domain controllers of the compromised system
▸Store LSA Secrets on Koadic
▸Use of three C2 channels; RDP, PowerShell Empire, and Koadic
Typically, ransomware and other types of malware are distributed via spam campaigns, questionable files or software download sources, Trojans, update tools, and fake software activation downloaded from unofficial sites. Cybercriminals often send emails with malicious files or web links within them. Its main purpose is to trick the recipients into opening the attached / downloaded file; then install the ransomware or other malware.



[…] Other reads:EtterSilent tool used by cybercriminalsPysa Ransomware – A Danger for your data […]
[…] also:Pysa Ransomware – A Danger for your dataThe First Ransomware in the world – When it all […]
[…] Also check:Remote Desktop solutions, how secure are these?Pysa Ransomware – A Danger for your data […]